About Mapsafe
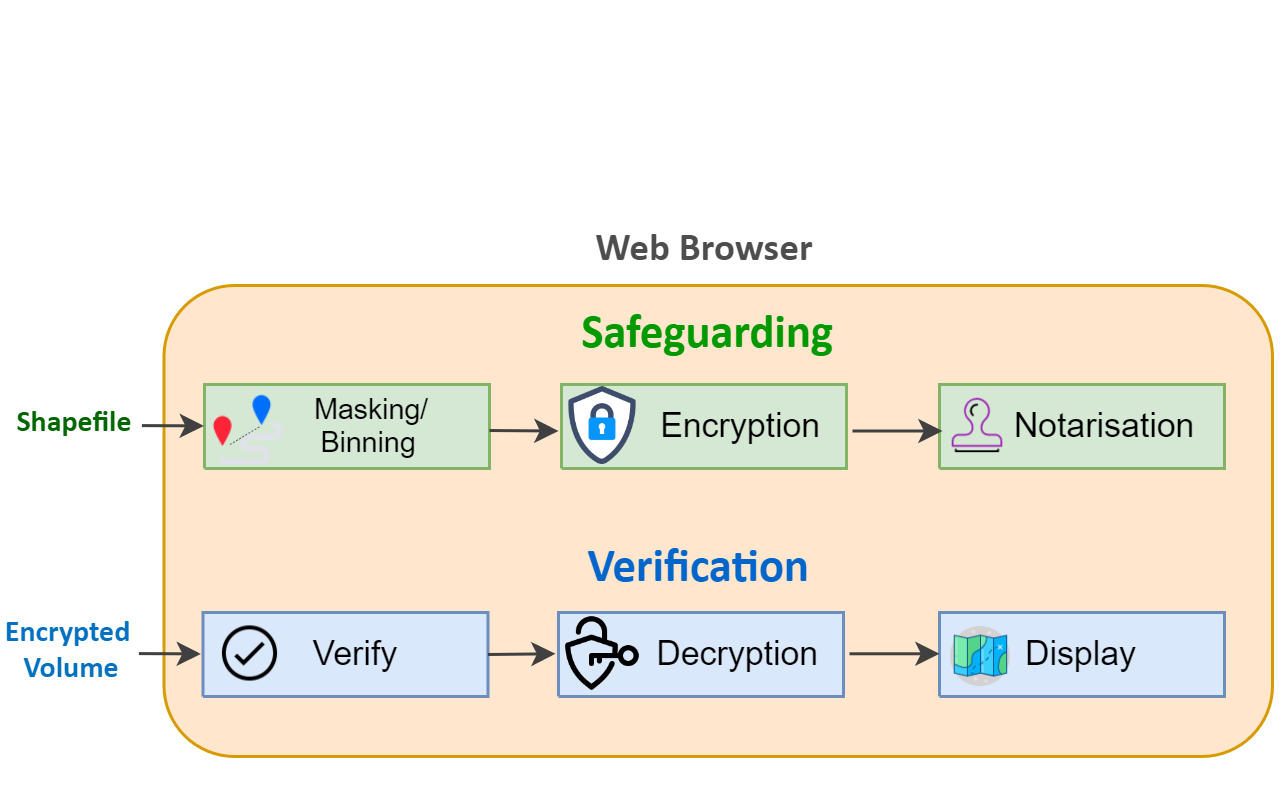
MapSafe completely safeguards sensitive geospatial datasets using obfuscation, encryption, and notarisation. These functions are implemented within the browser using popular open source JavaScript libraries without ever requiring users to install or download any software.
Whether you're a GIS expert, a GIS researcher, or a newbie, if you need to safeguard your geospatial data but aren't quite sure how, MapSafe makes your life easier and brings previously cumbersome geospatial data safeguarding methods into reach.